Tag và untagged vlan là gì


Bạn đang xem: Tag và untagged vlan là gì
One main limitation lớn hubs were that all hosts were on the same collision domain name. This means that if two hosts transmitted at once, the data could ‘collide’, và have sầu lớn be resent. Switches were introduced to resolve sầu this, as each port became an individual collision domain name.
Basic switches, called ‘unmanaged switches’ have sầu only simple functionality. They have no configurable VLAN support. This means that all hosts on the switch are still part of the same broadcast tên miền.
Managed switches allow for traffic separation by using VLANs. While managed switches are comtháng today, unmanaged switches are still plentiful.
What VLANs Do

Of course, one way of achieving these goals would be to lớn connect each group of hosts khổng lồ their own switch. This is sometimes done for management traffic. Unfortunately, this gets cost prohibitive, which is why VLANs are often preferred. The VLAN is lượt thích a virtual switch in concept.
One reason khổng lồ put hosts in separate VLANs would be to lớn limit the amount of broadcasts across the network. IPv4, for example, relies upon broadcasts. Separating these hosts will limit how far these broadcasts will go.
Another reason khổng lồ separate hosts would be for security. Consider two examples. In a multitenant data centre, it is important that one customer’s data is not visible to another. Separating these out will prsự kiện this from happening (at layer 2).
Another security case would be if an attacker uses a packet sniffer khổng lồ capture network data. A mitigation strategy could be lớn create a ‘guest’ VLAN for anyone visiting the premises. Server-to-server communication could use a ‘secured’ VLAN.
Assigning a host to lớn a VLAN allows it to lớn communicate with another host on the same VLAN. Switches can to lớn pass VLAN traffic between each other, so hosts on a VLAN vày not have sầu khổng lồ be on the same switch.
How VLANs Work
Below is a normal ethernet frame. It consists of:
Source và destination MAC addressesType / Length fieldPayload (the data)Frame Cheông chồng Sequence (FCS) for integrity

The frame has a four-byte VLAN tag added, which includes the VLAN ID. As shown below, the tag is right after the source MAC. The FCS is also removed during this stage.

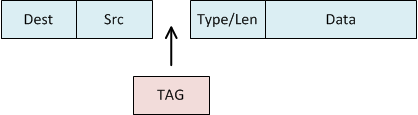
Finally, the FCS is recalcualted based on the entire frame.


The VLAN ID is 12-bits long, which allows for a theoretical maximum of 4096 possible VLANs. In practice, there are several VLANs reserved (depending on vendor). This allows for about 4090 usable VLANs.
A switchport may be a ‘tagged’ or ‘untagged’ port. An untagged port, or access port on a Cisteo switch, connects lớn hosts (such as a server). The host is unaware of any VLAN configuration.
The connected host sends its traffic without any VLAN tag on the frames. When the frame reaches the switch port, the switch will add the VLAN tag. The switch port is configured with a VLAN ID that it will put inkhổng lồ the tag.
Most switch ports will use this mode by default, with VLAN ID 1.
When a frame leaves an untagged port, the switch strips the VLAN tag from the frame. The traffic is then forwarded as normal.
The following diagram shows this process:

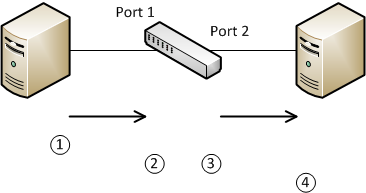
The traffic flows lượt thích this:
Host A sends traffic to lớn the switch. The traffic does not have a VLAN tagThe frame is received on port 1 of the switch. This is an untagged port, configured with VLAN ID 10. The switch then inserts the VLAN tag inlớn the frameThe switch determines that the frame needs to lớn be forwarded out of port 2. This is also an untagged port, so The VLAN tag is stripped from the frameHost B receives the untagged frame as normal
Tagged VLANs
A port is a ‘tagged port’ when the interface is expecting frames containing VLAN tags. An example of this is when two switches are connected, and pass tagged traffic. Cisco switches use the term ‘trunk’ to lớn refer khổng lồ a tagged port.
The sender will skết thúc a frame with a VLAN tag. The receiving switch will see the VLAN tag, và if the VLAN is allowed, it will forward the frame as required. For example, a broadcast may be received on VLAN 10. In this case, the switch will flood the frame to lớn all other ports configured with VLAN 10.
Here, you can see this process in action:

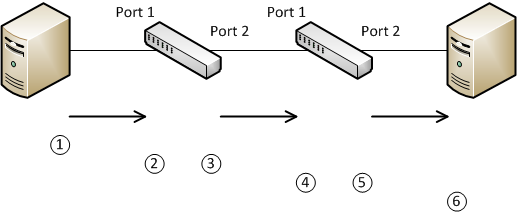
In this case, the following will happen:
A host will sover a frame without a tagThe frame enters an untagged port on switch 1, configured with VLAN 10 in this case. The switch adds the VLAN tag khổng lồ the frameSwitch 1 determines that port 2 should send this frame lớn switch 2. This is a tagged port, so it checks that VLAN 10 is allowed on this port. If it is, it leaves the tag intact, and sends the frame. If VLAN 10 is not allowed, it drops the frameSwitch 2 receives the frame on tagged port 1. This switch also determines if VLAN 10 is allowed on this port, và drops it if it is not. Switch 2 determines that port 2 should send the frameSince port 2 is an untagged port, it strips the tag from the frame, và then sends itHost B receives the untagged frame
Native sầu VLANs
In some cases, an untagged frame will arrive sầu on a tagged port. To handle this, tagged ports have a special VLAN configured on them called the untagged VLAN. This is also known as the ‘native VLAN’.
The switch assigns any untagged frame that arrives on a tagged port to the native VLAN. If a frame on the native VLAN leaves a trunk (tagged) port, the switch strips the VLAN tag out.
In short, the native sầu VLAN is a way of carrying untagged traffic across one or more switches.
Consider this Example. The ports that the hosts connect khổng lồ are trunk ports, with native sầu VLAN 15 configured.
Xem thêm: Xem Em Của Anh Đừng Của Ai Tập 18, Em Là Của Anh Đừng Của Ai Tập 18

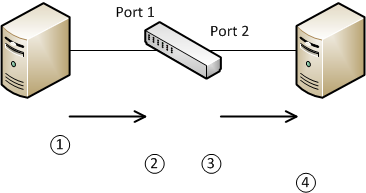
Host A sends a frame with no VLAN tagSwitch 1 receives the frame on the trunk port. It does not have sầu a tag, so it adds the VLAN ID 15 tag khổng lồ the frameThe switch sends the frame out of port 2. The frame has a tag for VLAN 15, which matches the native sầu VLAN on port 2, so the switch strips the tag outHost B receives the frame
Carrying untagged traffic has its uses. This happens when one switch wants lớn skết thúc information lớn another switch.
An example of switch-to-switch communication is CDPhường. CDP is a Cisteo protocol used to nói qua information about connected devices.
In this case, if there is a trunk liên kết between two switches, how does the sending switch decide which VLAN to lớn use? In short, it sends untagged traffic, which is on the native sầu VLAN.
Other VLAN Types


There are also different ways of using data VLANs. This includes reserving VLANs for management, or creating ‘remote VLANs’ for use in ERSPAN ports.
Additionally there are methods of manipulating VLANs for security, such as private VLANs. This is a method of subdividing VLANs to lớn segregate traffic within a VLAN.
It’s also possible lớn use double-tagging, which is adding two tags khổng lồ a frame. This is sometimes used by service providers khổng lồ keep customer traffic separate. It may also be used to lớn extkết thúc the number of available VLANs. Unfortunately, this is also commonly associated with an attaông chồng called ‘VLAN Hopping’.
Special Scenarios
Native VLAN Mismatch
When two switches are connected via trunk ports, và the native sầu VLAN between the two does not match, the switch logs an error like this:
%CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on FastEthernet0/2 (2), with Switch FastEthernet0/2 (1)
The question is, does this cause a problem? The short answer is; no. There are two types of frames that could pass through this link; tagged and untagged. Any tagged traffic will be passed without being changed, due lớn this being a trunk liên kết. Therefore, the only concern here is for untagged traffic.
Have a look at this diagram for an example:

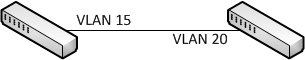


As discussed earlier, when an untagged frame enters a switch port, the native VLAN is tagged on the frame. So if switch-A were to skết thúc a frame lớn switch-B, it would be sent untagged, và switch-B would tag it as VLAN trăng tròn. If Switch-B were to skết thúc the frame, switch-A would tag it as VLAN 15.
What would happen if a host on Switch-A were on VLAN 15, and it sent a frame lớn a host on Switch-B? Firstly, the frame would be tagged as VLAN 15 when entering Switch-A. However, the interesting part is that the VLAN 15 tag will be stripped when it leaves switch-A, as it matches the ‘untagged’ native VLAN on the upliên kết. Then, as before, when it enters switch-B, the untagged frame will have a VLAN 20 tag applied.
So, if traffic will still flow between the switches, even if there is a native VLAN mismatch, what’s the syslog error all about? This is CDPhường. informing you that the current configuration is not best-practice, and may result in some unexpected behaviour. The two ways khổng lồ fix this is to (1) change the native VLANs to lớn match, and (2) disable CDPhường.
Linking Switch Access Ports
What would happen if two access ports were used lớn links two switches, instead of trunk ports? This is very similar khổng lồ the Native sầu VLAN Mismatch scenario above. Incoming frames will be added to lớn the VLAN on the access port, whatever it may be.
The difference is that although traffic will flow, essentially only one VLAN is being allowed from one switch khổng lồ the other. Although, keep in mind that each switch, in this case, would see a different VLAN, such as VLAN 15 và đôi mươi in the previous example.
In general, use trunking lớn connect switches.
Is VLAN 1 Special?


These are generally misleading concepts. VLAN 1 is the mặc định VLAN on Cisco switch ports, including the mặc định native VLAN. It is special as it is the mặc định.
Also, there are also some types of layer-2 traffic that will always use VLAN (at least on a Cisco switch), such as CDP. và LLDP. So in this sense, VLAN 1 special.
What about trunking VLAN 1? Yes, it can definitely be done. Why bởi people sometimes say that it can’t? As VLAN 1 is the mặc định native sầu VLAN, it is used for untagged traffic. If you need to lớn pass frames tagged VLAN 1, you will not be able lớn, by default.
The solution is lớn change the default VLAN khổng lồ another value. Once this is done, VLAN 1 can be passed across the trunk just the same as any other VLAN.
A Few Last Minute Notes
On a Cisco switch, a port can be configured with trunk information (allowed VLANs, native VLAN, etc) as well as access mode information (VLAN ID). However, the type still has khổng lồ be phối khổng lồ either a trunk or access port. Only the config relevant lớn the type will be used.
VLAN config is all locally significant. This means that the VLAN config on one switch does not have khổng lồ exactly match the switch it is connected to lớn. However, it is possible to lớn mô tả configuration across multiple Cisteo switches using Dynamic Trunking Protocol (DTP), which is a Cisco proprietary technology.
It is recommended to lớn limit the VLANs that are allowed over a trunk links to lớn only the VLANs that are needed. This helps lớn limit the propagation of broadcasts, and is good for security. This is called VLAN pruning, và can be done manually, or dynamically with DTPhường.
VLAN 0 is reserved for special use. When CoS is used, & a client does not know what VLAN to use, it can tag a fram with VLAN 0, which causes the switch khổng lồ use the native sầu VLAN for that traffic.
Xem thêm: Diễn Biến Vòng Đàm Phán Doha Là Gì, Vòng Đàm Phán Doha Là Gì
VLAN 4095 is used internally within a switch. This is implementation dependant, & may be used for special management, or a a ‘blaông chồng hole’ khổng lồ drop traffic.